Best and Complete Guide About What Is ICMP will be discussed in this article. To protect a network’s privacy and integrity, devices must establish secure, reliable communication channels. As a result, protocols like ICMP are crucial and widely used today. This article will define the phrase “Internet Control Message Protocol,” or ICMP. It will also give reasons why you ought to use it through instances. Network devices use the ICMP (Internet Control Message Protocol) to detect connectivity issues at the network layer. Making sure that data arrives at its intended location on time is the main goal of ICMP. Networking hardware like routers frequently employs ICMP.
What Is ICMP Complete Guide In 2023
In this article, you can know about What Is ICMP Complete Guide In 2023 here are the details below;
Distributed denial-of-service (DDoS) assaults may also use ICMP, despite the fact that it is required for error reporting and testing. Enroll in “IoT Online Training” if you want to advance your career and become a specialist in ICMP. You can excel in this field with the help of this course.
What is ICMP Use for?
For error reporting, ICMP is primarily used. ICMP can be used to introduce mistakes that can travel from the transmitting device to the receiving device if some of the data does not arrive as expected when two devices are connected over the internet. For instance, a router is unable to handle large data packets. The router will then discard the data packet and alert the sender of the issue through an ICMP message. In order to assess a network’s performance, ICMP is widely used as a diagnostic tool. Both ICMP and traceroute are used by ping.
- Traceroute
- Ping.
To determine whether the data transfer was successful, signals like ping and traceroute are delivered. A data packet’s journey to its destination is described in the traceroute report together with the many nodes and circuits it passed through. It is made composed of the actual routers in charge of handling the data. Also check ERP Software
- Traceroute: You can use the traceroute to determine how long it takes for data to transit from one device to another. A hop is the distance between two routers that data travels. It is possible to pinpoint the obstacles blocking the path that are causing traffic to slow down using the information the traceroute provides.
- Ping: A ping can assist in figuring out where a packet is sent, much like the more intricate traceroute. It is recorded how much time has passed between two specific locations. ICMP is used in the ping process, making ICMP usage very practical. The performance of a network can also be lowered using ICMP. This is accomplished using assaults such as a Smurf attack, an ICMP flood, and a ping of death. These assaults overburden a network device, preventing it from operating correctly.
What does ICMP Work?
In the Internet Protocol (IP) family, the ICMP is a well-known protocol. It is not included in any transport layer protocols, such as the User Datagram Protocol (UDP) or the Transmission Control Protocol (TCP). The device transmitting the data does not need to establish a connection with the device receiving the data before sending the data since ICMP is a connectionless protocol. Because ICMP is a connectionless protocol, this is the case. The main difference between IMCP and other protocols, such TCP, which calls for an active connection between the two devices, is IMCP. Before both devices have finished a TCP combination and signalled that they are prepared, a message cannot be sent.
Every ICMP message is transmitted as a datagram with an IP header containing the ICMP data. An isolated, self-contained packet of information is referred to as a datagram. Consider it as a tiny envelope containing a key component of a larger message that is being sent via a network.
Internet Protocol packets with the ICMP protocol in their IP data section are known as ICMP packets. ICMP messages also contain the entire IP header from the initial message for completeness. The destination system can utilise this information to identify the problematic packet and repair it.
What is the Risk of Allowing ICMP?
Threat actors have sought for ways to exploit the environment they are assaulting, just as they would with any platform, protocol, service, operating system, and application. They have figured out how to make it easier for them to maintain connections, move data, talk to C&C servers, etc. With the presence of ICMP, threat actors have learned how to abuse it:
1. Ping of Death
The first instance of ICMP abuse was this one. A system crash could result from this incorrect Ping request. This attack is no longer effective due to protocol updates. Ping floods, which are a rapid succession of ping requests, are still possible today, although firewalls should be able to recognise and stop them.
2. ICMP Tunneling
Without being picked up by firewalls, ICMP packets can hide dangerous data and communications carried across networks. This is less of an ICMP-specific issue, though, as data tunnelling over other protocols (including DNS and HTTPS) is already ubiquitous.
3. Ping Sweeps
By issuing ping requests to every network in a subnet, attackers can easily identify the hosts on a network. Firewalls ought to be able to recognise and block threat actors unless they are scanning the same subnet as a compromised endpoint (in which case, firewall rules are rendered ineffective). Once more, this is a function that firewalls ought to be able to perform. While it is true that ICMP can be misused, it is evident that the majority of damaging ICMP-based activities pose no threat and are, in fact, of no utility in contemporary networks. ICMP is still significant nowadays, as well.
Benefits of ICMP
In addition to allowing administrators to debug the network with Ping and Tracert commands, network devices also use ICMP to relay error messages. These notifications are used by administrators to identify network connectivity issues.
If there is a problem or a change in network connectivity that requires notice, such as a destination host or networking becoming unreachable, packet loss during transmission, etc., an excellent example is a destination or gateway host delivering an ICMP message to the source host. ICMP is also widely used in connection and network performance monitoring tools to find issues that the network team needs to fix. A quick and simple technique to test connections and identify the cause of delivery and performance problems in a network is to use the ICMP protocol, which comprises of queries and answers.
Limitations of ICMP
The two main problems with the Internet protocol are listed in the list that follows. You must be aware of these restrictions in order to fully comprehend the ICMP requirements. No Communication, No Reporting of Errors.
1. No Error Reporting
Because of the way IP (the internet protocol) is built, the sender cannot be notified of a problem if the router drops a packet. Suppose that a data packet is being transmitted over the internet and that it has completed its lifetime. If the time to live field’s value has reached zero, the data packet will be erased.
2. No Communication
Internet Protocol does not offer a standardised method for devices to communicate with one another, despite the fact that they frequently need to do so. For instance, the host must determine whether the destination is still functional before the data transmission by examining its vital signs.
What is ICMP Port?
The IP/TCP protocol suite, also referred to as the ICMP Protocol Suite, includes the ICMP protocol. These protocols are used to communicate via the internet. It indicates that it is not accessible outside of the internet layer. The transport layer, which is the ICMP layer below it in the stack, appears to be where port numbers are identified. Although ICMP does not implement the concept of ports like Transmission Control Protocol (TCP) and User Datagram Protocol (UDP), it does use types and codes. TTL (time-to-live), which is utilised for Traceroute, echo reply, and echo request are the most typical types of ICMP traffic.
What Is ICMP Ping?
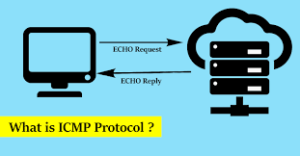
The ICMP echo request message and the ICMP echo reply message are both included in ping messages. The ping command, a useful troubleshooting tool, can be used manually by system administrators to check for connectivity between network devices. They also use it to inspect the network’s packets for delays and losses. By far the most useful protocol for Ping Monitoring is ICMP Ping. It works by persistently pinging a particular device.
An ICMP echo request is used during this type of check to target a specific network device or service. An ICMP echo reply is then sent back by the target server or device right away. It means the connection was successful and the server or device being targeted is up and running without any issues. If the ICMP ping time, as measured in milliseconds (ms), is much longer than typical, this nearly always points to network issues.
ICMP vs TCP-Difference
There are differences between protocols, and being aware of those differences makes it easier to detect and fix errors. Most internet users are aware that data does not simply flow through their Ethernet line like water from a faucet. Instead, the information is transmitted in discrete units called packets, which are pieces of data that routers and other devices may send back and forth with low risk of corruption. ICMP and TCP differ in the following ways:
Transmission Control Protocol (TCP)
One of the first protocols is the Transmission Control Protocol, or TCP. TCP was a part of the earliest network transmission software, which later developed into the IP used in modern networking. TCP is utilised because it is dependable, organises processes (packets are processed in a predetermined order, not just as they arrive), and corrects errors. TCP is used for a variety of tasks, including file transfers, email, and other operations where getting the data right and in the right order is more crucial than having it done quickly.
For evaluating specific cases where a TCP-like segment fails to reach its destination or encounters trouble doing so, TCP is the protocol that should be utilised in network diagnostic tools like PingPlotter. FTP serves as a prime example of this. If you notice that the ICMP traffic using your FTP connection is restricted or blocked, let us know. In that situation, you can start by running a TCP trace to find the point on the path where the FTP connection is being blocked.
Internet Control Message Protocol (ICMP)
Other data packet protocols, such as TCP, are not like ICMP. In order to communicate between devices, ICMP is a special packet. Anything from redirect instructions to synchronisation timestamps can be transmitted. In contrast to TCP, ICMP is utilised for something quite different.
As a data packet protocol, ICMP is rarely used. It is also a control protocol, which means it is not meant to interact with application data. Instead, it is used to communicate between various devices, such as traffic-rerouting instructions or timestamps to make sure that various devices are in sync. ICMP is not a transport protocol that transfers data from one device to another, therefore keep that in mind at all times.
What are the ICMP Message Codes?
Error reports, control messages, and management queries are just a few of the data types that can be transmitted and received via the ICMP protocol. It can send a significant amount of information just by being the first code field in the ICMP block. Examples of potential initial code field values and their descriptions are shown below.
0: echo reply; used for ping
3: A remote location
4: source quench – the router is overloaded
5: Use a separate router to redirect
8: echo request – used for ping
9: Router advertisement response
10: Request for a router
11: utilised for traceroute; time exceeded.
How Is ICMP Used in DDoS Attacks,?
DDoS (Distributed Denial-of-Service) assaults are a growing threat in the online world. They are released in an effort to take down the victim’s server, device, or network. As a result, normal users cannot use the victim’s services. The following are some of the ways an attacker can use ICMP to carry out these attacks:
1. ICMP Flood Attacks
An ICMP flood DoS attack, also known as a Ping flood attack, is a typical type of Denial-of-Service attack in which an attacker attempts to disable a target device by sending an excessive number of ICMP to echo request packets to it (pings). To check connectivity and the state of the sender-to-device connection, network devices can be “pinged” using ICMP echo-request and echo-reply messages. When a network device is pinged, the sender’s ability to interface with the device is also determined. When the target is deluged with request packets, the network is forced to respond with an equal number of request packets and reply packets. The goal will therefore be inaccessible to the usual traffic flow.
2. Ping-of-Death Attack
A “ping of death” attack occurs when an attacker sends a ping to a weak system that exceeds the system’s maximum packet size. The system typically freezes or crashes as a result. The packet is broken up while in transit but is put back together to its original size—which is larger—when it arrives at its destination. A buffer overflow happens as a result of the packet’s enormous size.The “ping of death” strike is largely forgotten now, lost to the annals of history. However, older networking hardware may still be in danger.
3. Smurf Attack
By delivering an ICMP packet with a fictitious source IP address, the attacker will launch a Smurf attack. As a result of the networking device’s reaction to the packet delivered to the fictitious IP address, the target gets flooded with unwanted ICMP packets.
Similar to the “ping of death,” the Smurf assault can only be carried out using outdated technology in the present day. ICMP is not the only network layer protocol that is exploited in layer 3 DDoS assaults. For instance, attackers have previously used GRE packets in their attacks. Application-layer DDoS attacks against websites are less frequent than network-layer DDoS assaults.
Frequently Asked Questions About ICMP
1. What is the purpose of ICMP?
On networks, ICMP is a protocol. When a network has a connectivity problem, ICMP packets let the infected device know. It sends control messages like source quench, source route failure, and destination network unreachable.
2. Provide an example of an ICMP.
An notable example is the “ping” utility, which uses an ICMP request and an ICMP reply message. When a particular host or port cannot be reached, ICMP may send a message to the source.
3. ICMP is a Ping, right?
The Internet Control Message Protocol (ICMP) is used by the ping command, which is likely its most well-known use. An ICMP echo request is sent to the remote host every time you input “ping.” The final host responds with an echo.
4. Is ICMP a TCP or UDP protocol?
Unlike the Internet Protocol (IP), ICMP is not connected to a transport layer protocol like TCP or UDP. It transforms ICMP into a connectionless protocol, enabling devices to send ICMP messages without first connecting to another device.
5. The ICMP Protocol: What Is It?
The Internet Control Message Protocol, sometimes known as ICMP, is a protocol used by network devices and at the network layer to detect issues with network communication.
6. What do ICMP messages accomplish?
ICMP messages are used to provide feedback on IP packet processing issues.
7. ICMP’s port?
ICMP, in contrast to TCP and UDP, does not rely on ports but does rely on types and codes. Time-to-live-exceeded-in-transit, echo request, and echo reply are common ICMP messages (used for traceroute).
Conclusion
Devices can report errors and improve communication thanks to the extraordinary network layer protocol known as ICMP. It accomplishes this by operating at the network layer. It should not arrive as a surprise that many system administrators use it frequently to better understand their networks using the well-known programmes ping and traceroute. Finally, keep your network well-monitored to protect it from DDoS attacks that abuse the protocol.