Torrents come from one of the best file distribution mechanisms ever created, BitTorrent. Unfortunately, torrents have been strongly associated with piracy. Logically, when people found a reliable way of transferring large files over many users, online pirates took it to transfer copyrights media and profit.
Today, going down the road of torrenting and BitTorrent is risky; its waters are infested with copyright preying eyes and unnecessary regulations.
In this post, we’ll show you how to torrent anonymously. We’ll learn how using the right type of torrent servers, VPNs, and Seedboxes can protect your identity.
1. Are Torrents Illegal?
Torrenting and almost any P2P-related file-sharing activity have a very close relationship to piracy. But these file-sharing mechanisms are just that…. Tools made for sharing/distributing files. It is what online pirates do with a torrent that is illegal.
Take, for example, the most basic file transferring mechanisms, FTP and HTTP have also been used to widely distribute copyrighted material. But FTP and HTTP are also not illegal; it is what people do with them that may fall into the unlawful and legal side.
BitTorrent is not only used by pirates, but it is also used within legal boundaries, by famous companies. It is used by Facebook and Twitter to push updates to all of their distributed servers; it is used by research institutes to distribute extensive data to remote stations, it is used by Linux to offer an alternative download for Ubuntu OS.
If you download the latest Ubuntu version via a torrent file found on its official site, you are not breaking the law. But if you are logging into public torrent sites like The PirateBay, RARBG, or 1337x, downloading their torrents (which in most cases are copyright material), you are breaking the law.
2. How Do Torrents Work?
Torrents are the files used by the P2P distribution mechanism, known as BitTorrent. Not to confuse with the BitTorrent client; other clients are uTorrent, Transmission, Deluge, etc., which also use the same mechanism.
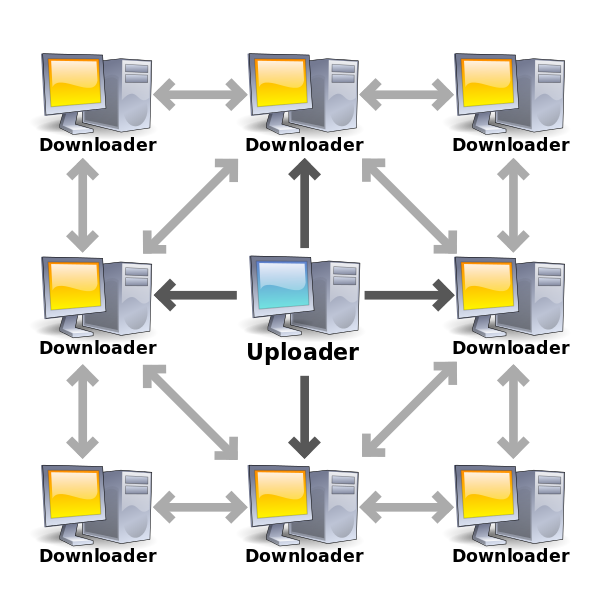
BitTorrent uses a central server, a torrent tracker, to open and coordinate communication among peers (sharing users). This server does not help transfer any content data; it only helps build a relationship between peers around the same set of torrent files.
Once a relationship is established, all members become uploaders and downloaders.
BitTorrent does not use any built-in search engine, as previous P2P services as Napster and Gnutella did; instead, users have to go to (public or private) sites to download torrent files. BitTorrent also splits the file into pieces. With the help of the coordination of the tracker, pieces of the file can be distributed among peers within a swarm. Breaking a file helps a faster and more robust distribution of files.
In a private tracker, everyone in the swarm is a known member, so private trackers tend to be safer places. But file-sharing can be insecure if you are using public trackers.
3. So Where Is Their Privacy Flaw?
When you use public torrent sites like PirateBay or 1337x, the torrent files you’ll get from those sites will come with public trackers. These public trackers do their job right, but they are infested with all kinds of personalities, from good citizens that know the value of sharing, the leechers, who download what they want and run away, and then the copyright trolls.
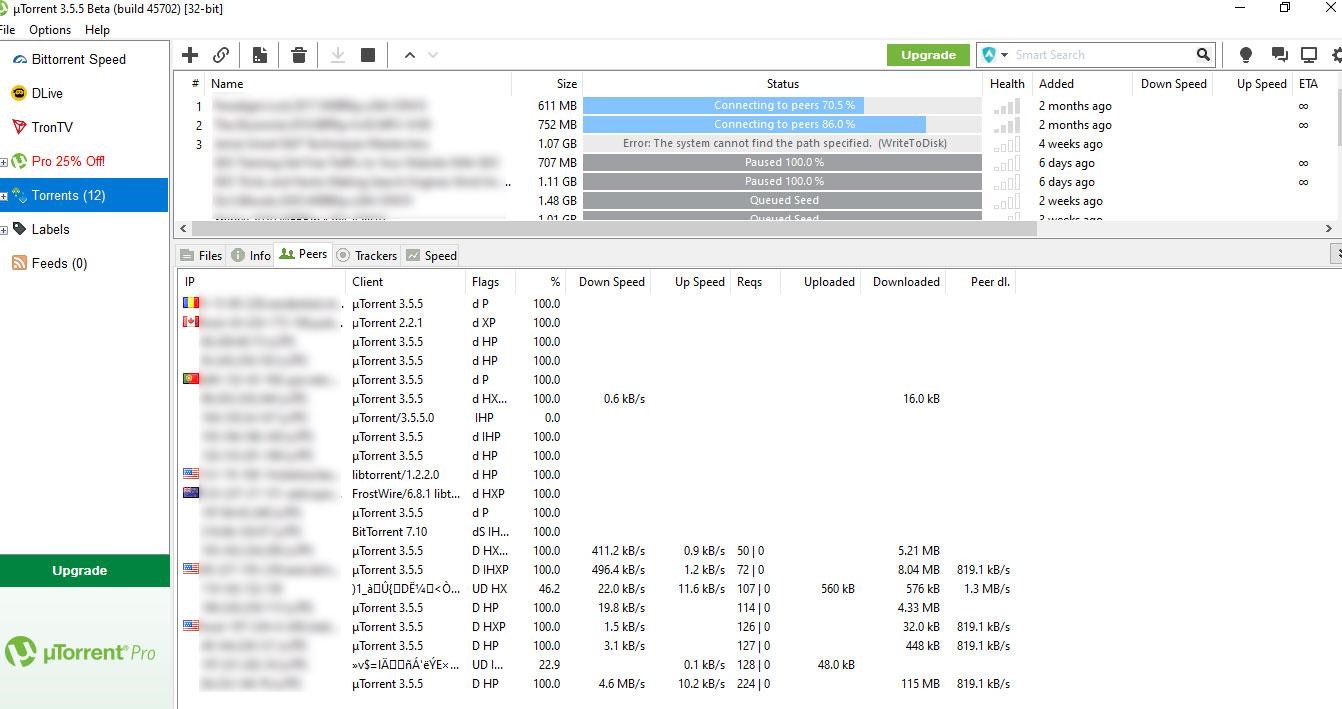
So, when you load a torrent file into your favorite torrent client, the client will instantaneously establish communication with the tracker. Of course, you can optimize the torrent client, but by default, the tracker joins you with the right swarm (the one who shares the same interest on the same file). To join you with the swarm, the tracker needs to share your public IP to all the peers, and these peers might include those personalities above.
Look at all the peers found along with information such as country, IP, torrent client, etc., in seconds… while downloading a copyright file from a public tracker.
Additionally, your local ISP can also identify BitTorrent traffic (via port number). The outgoing and incoming traffic that uses your local ISP’s pipes can be inspected. They can identify the “Top Talkers” IPs consuming the most bandwidth and what application they are using, in your case, BitTorrent. Although they can’t legally inspect the data within a packet, (so they don’t know if you are transferring copyright content), they will eventually throttle your bandwidth, just for using BitTorrent.
4. How To Torrent Anonymously?
There is no scape in downloading a file and not sharing your IP information. But still, there are ways to protect yourself in the swarm and from ISP inspection, and download your favorite torrents.
So, how to download torrent anonymously?
1. Use a private tracker.
As mentioned early, public trackers may compromise your identity. As they are places full of unidentified people, and you might be the unlucky one to meet with a copyright troll… especially if you are downloading blockbusters every time.
Instead of going to public trackers, look for private trackers. Now, bear in mind that these communities are PRIVATE, and they intend to keep it that way. So it is tough to become a member here.
What are some of the private tracker’s requirements?
- You’ll have to be invited. You can’t just sign in and pay. It doesn’t work like that.
- You’ll have to keep a good sharing ratio. Sharing more than what you download is a strict requirement. That means you’ll have to be 24X7 uploading torrents.
2. Use a VPN.
Within the context of a P2P swarm, what a Virtual Private Network (VPN) does is that it puts a mask on your sensitive information. With a VPN, you are still connecting to a torrent swarm, but you are pretending to be somebody else.
VPNs were built to extend Local Area Networks to far away geographical areas via public networks (Internet). So protecting their back and forth communications require encryption algorithms in place.
When you torrent with a VPN service, instead of using your IP in the swarm, you are using the VPN’s server IP. How to torrent correctly with a VPN?
- Not all VPNs allow torrenting. Make 100% sure they allow torrents, and if they don’t, and you download anyways, you might get into trouble. The reason is that some VPN providers have servers in countries with strong regulations towards copyright material.
- Make sure they have a zero logs policy. Some VPN providers keep logs. If they do, all your torrenting information and history will be recorded. If a copyright troll finds the VPN server IP, he or she might request logs under lawsuits and fines.
- Make sure Kill Switch is available. Kill switch is a feature that disconnects the access to the Internet if the VPN disconnects for some reason. This ensures that when torrenting, you are always protected.
3. Use a Seedbox.
A Seedbox is a whole new level for torrenting. A seedbox not only ensures anonymity but takes your entire torrenting experience to the next level.
So, a seedbox is a cloud-based server, provided as a managed service. The seedbox providers build theses boxes, especially for torrenting and improving the sharing ratio of private trackers. So a seedbox gives you 10x more security and anonymity than a VPN because you are not using your computer/home Internet (ISP) to download and store torrents. Additionally, seedboxes are usually based in data centers located in countries with “friendlier” data laws, and they don’t just allow torrenting, they encourage it!
How to torrent with a Seedbox?
- Log into the remote seedbox. Log in to the remote server using some remote connection, SSH, web console, HTTPS, or anything that allows you to manage the server remotely.
- Download the torrents using a high-speed seedbox. Once in the remote server, you will open the torrent client (often comes pre-installed in the seedbox), and start downloading torrents at high speeds.
- Either stream content remotely or transfer it to your local computer. Seedboxes come with streaming media servers (usually Plex or Kodi) to stream all your media content online. If you want to have it locally, you can transfer all media using secured methods, such as SFTP, FTPS, or RSync.
Final Words.
The torrent swarm is where the magic happens— it is sharing at its maximum, but ironically this is also the place where things can go really wrong. So, everything that you do to stay anonymous while torrenting is a matter of protecting yourself within the swarm.
Remember, you are assigned to a swarm, by a torrent tracker, so using private trackers will help you avoid meeting copyright trolls and leechers. Second, try using a VPN, but make sure they allow torrents, and finally, torrent with a seedbox. The level of anonymity, speed, and extra features of a seedbox is impressive.