Wi-Fi Security WEP Vs WPA Or WPA2 will be discussed in this article. Wi-Fi security technologies that protect wireless connections are WEP, WPA, and WPA2. They prevent hackers from accessing your network, conceal your data, and safeguard your communications. WPA2 is generally the best option, even though protecting your network with it requires more processing power. Find out more about Wi-Fi security settings and how to increase your protection using encryption technologies like VPNs.
Wi-Fi Security WEP Vs WPA Or WPA2
In this article, you can know about Wi-Fi Security WEP Vs WPA Or WPA2 here are the details below;
What are Wi-Fi security protocols and are they encryption tools?
Encryption technology is used by Wi-Fi security protocols to safeguard networks and client data. Wireless security methods are important for keeping you safe online because wireless networks are frequently less secure than wired ones. These days, WEP, WPA, and WPA2 are the most widely used Wi-Fi security methods.
This Article Contains:
- Are encryption technologies included in Wi-Fi security protocols?
- Wired Equivalent Privacy, or WEP, is what?
- What is WiFi Protected Access, or WPA?
- WPA2: What is it?
- Comparison of WPA, WPA2, and WEP
- The technical specifications of WEP, WPA, and WPA2.
- And WPA3?
- What are tools for Wi-Fi encryption?
- Use Avast SecureLine VPN to increase Wi-Fi security.
Tools for data encryption mangle private information till it becomes unintelligible. Cryptographic keys are operated by Wi-Fi security protocols to randomize data & render it unintelligible. The same key is used for both data encryption and decryption since Wi-Fi systems employ symmetrical encryption.
The non-profit group that controls the Wi-Fi trademark, the Wi-Fi Alliance, has certified all Wi-Fi security protocols. At the moment, there are four wireless security protocols available:
- Equivalent Privacy over Wire (WEP)
- Protected Access via WiFi (WPA)
- Protected Access 2 (WPA 2) over WiFi
- WPA 3 (Wi-Fi Protected Access 3)
What is WEP( Wired Equivalent Privacy)?
Wi-Fi security protocol that is most widely used and oldest is called WEP (Wired Equivalent Privacy). It was the privacy feature that was included in IEEE 802.11, a collection of technological standards designed to give wireless local area networks (WLANs) a security level that was on par with conventional LANs.
In 1999, WEP was approved as a security standard by the Wi-Fi Alliance. WEP, which was formerly said to have the same security advantages as a wired connection, has been beset with numerous security issues over time. Furthermore, these vulnerabilities have gotten worse as processing power has increased. Even with upgrades, WEP is still susceptible to security lapses. In 2004, WEP was formally decommissioned by the Wi-Fi Alliance.
Any systems that continue to use WEP need to be upgraded or changed.
What is WPA (WiFi Protected Access)?
In order to address the increasing vulnerabilities of its predecessor, WEP, WPA (Wi-Fi Protected Access) was introduced as a wireless security protocol in 2003. Because the WPA Wi-Fi protocol employs a 256-bit encryption key—a significant improvement over the 64-bit and 128-bit keys used by the WEP system—it is more secure than the WEP protocol.
WPA additionally makes use of the Temporal Key Integrity Protocol (TKIP), which creates a new key on-the-fly for every packet, or data unit. When compared to WEP’s fixed-key scheme, TKIP is far more secure.
WPA is not without problems, though. WPA’s fundamental technology, TKIP, was intended to be installed on WEP-capable devices through firmware updates. As a result, WPA continued to rely on components that were simple to hack.
What is WPA2?
The double iteration of the Wi-Fi Protected Access wireless safety protocol is called WPA2 (Wi-Fi Protected Access 2). Similar to WPA1, WPA2 was created with Wi-Fi network security and protection in mind. Only those who possess your network password can access the encrypted data that is broadcast or received over your wireless web thanks to WPA2.
The Advanced Encryption System (AES) was introduced by the WPA2 system as a benefit, taking the place of the more susceptible TKIP system in the original WPA protocol. AES offers robust encryption, which is used by the US government to safeguard confidential information.
Regrettably, WPA2-capable access points—which are primarily routers—remain susceptible to WEP assaults, much like its predecessor. Disable WEP and, if at all possible, confirm that the firmware of your router does not depend on WEP in order to close this attack vector.
WPA vs WPA2
Wireless networks are secured by two security standards: WPA (Wi-Fi Protected Access) & WPA2 (Wi-Fi Protected Access 2). The Wi-Fi Protected Access security standard, known as WPA2, is better secure than its ancestor, WPA. It is the second version.
It’s likely that your Wi-Fi router supports both WPA and WPA2 security protocols. Select WPA2 when enabling Wi-Fi encryption on your router for the highest level of security.
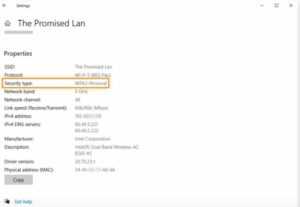
Navigate to the Wi-Fi settings menu from the Windows Start menu to verify your Wi-Fi security protocol. After selecting the WiFi network to which you are connected, select Properties.
The kind of wireless security protocol that your Wi-Fi networks employ can be seen in the Windows Wi-Fi settings.
Keep in mind that WPA2 needs more processing power to defend your network if your machine is older. However, this only affects older access points that have been updated to use WPA2 firmware. The majority of modern access points have hardware that can easily process WPA2.
Check read our tutorial on computer speeding up or learn how to speed up your internet connection if your connection is still slow even with latest technology.
WEP vs WPA vs WPA2
When it comes to ensuring your Wi-Fi network, WPA2 is usually your best option because it is the most contemporary wireless security standard. Let’s examine the benefits and drawbacks of each security protocol in descending order of importance.
WPA2:
Pros:
- resolves a number of security issues with its predecessors
- use the most robust encryption technique: AES
- The Wi-Fi Alliance mandates that it be used on all Wi-Fi certified equipment.
- 256-bit encryption keys
Cons:
- still has certain security flaws
- most processing power is needed.
WPA:
- fixes the security flaws in the original Wireless Ethernet Protocol (WEP) standard.
- The TKIP encryption technique outperforms WEP’s fixed-key encryption.
- 256-bit encryption keys
Cons:
- When TKIP is implemented on WEP devices, it might be misused.
- Comparable WEP security flaws
WEP:
Pros
- Not by much, but better than no security protocol
Cons:
- Overflowing with security flaws
- Encryption requires only 64-bit and 128-bit keys.
- encryption with a fixed key
- challenging to set up
What about WPA3?
The most recent wireless security standard, known as WPA3 (Wi-Fi Protected Access 3), encrypts data using Perfect Forward Secrecy, a frequent and automatic encryption type. Although not as frequently used as WPA2, it is more secure than the latter. WPA3 isn’t automatically supported by all gear, and using it frequently necessitates expensive updates.
What are Wi-Fi encryption tools?
When utilizing Wi-Fi networks, Wi-Fi encryption solutions assist protect both your device and your data. Unsecured wireless networks may be full of security holes that hackers and other criminals might use to steal information or launch malware assaults. WPA2 and other Sp Wi-Fi security methods are now considered standard for protecting wireless networks.
However, internet safety doesn’t end there. There are numerous methods available to assist defend your network, including proxies, VPNs, and Tor. Privacy protections will benefit even your most trusted gadgets; additional privacy apps are even necessary for iPhones. But not every tool has the ability to encrypt data.
To keep your Wi-Fi network secure, use a Virtual Private Network (VPN), which offers robust encryption protections. Typically, your Internet Service Provider (ISP) handles the transmission of your website traffic. However, while using a VPN, a VPN server routes and encrypts your traffic first.
This implies that instead of coming from your router, your data and communications appear to be coming from the VPN server. Put otherwise, your privacy is increased since not only is your data encrypted, but it also appears that all of your communications are coming from the VPN server.
Why a VPN is necessary if you use Wi-Fi security protocols may be on your mind. VPNs enhance the baseline security offered by regular Wi-Fi security mechanisms. All of your internet traffic is sent to a VPN server, protecting your online activities from prying eyes like your ISP, the government, hackers, and others. Additionally, a VPN enables you to access your preferred online material without being blocked by geo-blocked networks and to browse securely on public Wi-Fi.
VPNs and Wi-Fi security mechanisms can cooperate to keep you safe online. WPA2 and other Wi-Fi security methods guard your local network from hacks and breaches, while VPNs encrypt all of your outbound internet traffic.
Boost Wi-Fi security with Avast SecureLine VPN.
In order to prevent hackers from accessing your local network, Wi-Fi security procedures are crucial. However, protecting you and your family online requires fighting on multiple fronts. Increase the security of your wireless network by adding Avast SecureLine VPN to your toolbox.
Bank-grade encryption is offered by Avast SecureLine VPN to help shield you from online risks like scammers and hackers. To conceal your activities from your ISP, the government, and other prying eyes, use Avast’s VPN. Utilizing Avast SecureLine VPN in conjunction with robust, industry-standard Wi-Fi security mechanisms will safeguard your network from all angles.